You’ve just been handed a vulnerability scan report run by your security consultant, and you have been tasked with remediation. You are browsing the Exploitable Vulnerabilities Report and come find that you have hundreds of systems at the top of the list impacted by SMB Signing not required. How do you go about remediation?
By remediating this vulnerability, you are really aiming to reduce the impact of a man-in-the-middle scenario, specifically the use of NTLM Relay attacks. When not addressed, this vulnerability can be a fairly quick path to some level of system access. Often, privileged access in an on-prem client/server Windows network is almost a certainty given enough time.
Every system showing this vulnerability will need the following setting enabled:
Computer Configuration\Windows Settings\Security Settings\Local Policies\Security OptionsMicrosoft network server: Digitally sign communications (always)Setting: Enabled
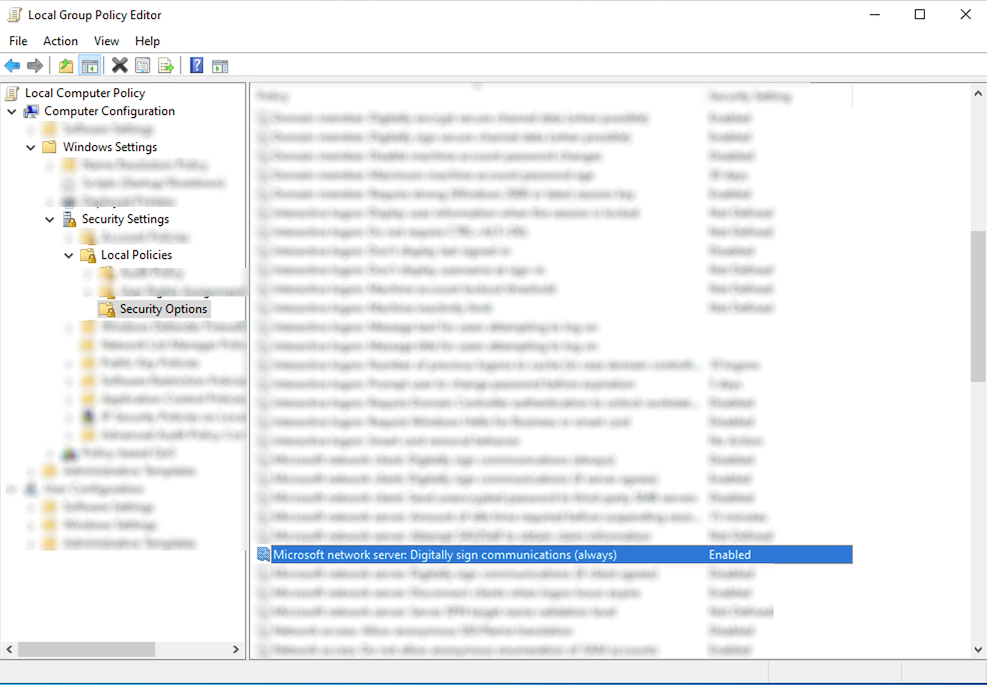
Deploy via Local Group Policy Editor or AD GPO.
Are there compatibility concerns?
Potentially, but generally it is fairly safe today. You will have to do a bit of digging/testing to see if any of your systems are impacted by the change.
