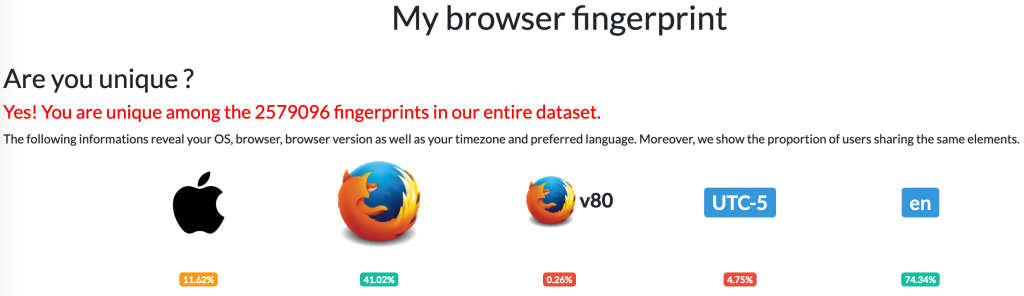
AmIUnique
Most understand that their source IP address is associated with their web browsing session. Did you know that your IP address nearly doesn’t matter due to the fact that your browser fingerprint is comprised of many things such as your browser, browser version, operating system, OS version, time zone, browser settings, fonts, graphics capabilities, and others? By asking for and collecting this information with each page visit, and due to the variety of combinations, web servers are able to correlate browsing session to individuals no matter the source IP address.
Cisco’s Talos Intelligence Group is one of the largest commercial threat intelligence teams in the world. Look up IP or domain reputation, file reputation based on hash, and more. You can also find blog posts, podcasts, and other cybersecurity related content.
“Cybercrime Support Network (CSN) is a public-private, nonprofit collaboration created to meet the challenges facing millions of individuals and businesses affected each and every day by cybercrime.”
In our physical world, victims of crime have resources to reach out to. Where do victims of cybercrime go for help? FightCybercrime.org provides resources for reporting and recovering from incidents such as cyber-bullying, scams, identity theft, fraud, and others. Check out the resource library for infographics, posters, checklists, and sheets related to gambling, COVID-19, robocalls, and other scams.
‘;–have i been pwned?
Have I been pwned (rhymes with owned, but begins with ‘P’) is a website that tracks breaches and allows users to check and see if their associated email address (and subsequent data) has been compromised. Simply enter your email address, and if a match is found, you will see which breaches are associated and what type of data was also stolen. It may include names, passwords, password hints, genders, birthdays, IP addresses, and others.
What does this mean? Consider the hundreds of websites we all use for some service. Whether it be an email account, social media, online shopping, utilities, banking, games and so many others, they all typically require a user account to be created in order to use them. They also typically require some personal information such as date of birth, gender, mailing address, etc. If that website suffers a breach, your personal information could potentially be in the hands of bad actors. Additionally, if you use the same username and password, or answers to security questions, you could now be susceptible to additional hacking across the various sites and accounts you use. Take a look at the list of breaches the tool indexes; many familiar organizations can be found.
What can be done to limit the use of stolen data? For individuals, using unique and strong passwords across all sites with a password manager goes a long way. Additionally, using non-answers to security questions can further increase the difficulty for bad actors. Many answers to security questions can be found via social media. Additionally, enabling multi-factor authentication where possible further protects your accounts.
Department of Homeland Security National Terrorism Advisory System
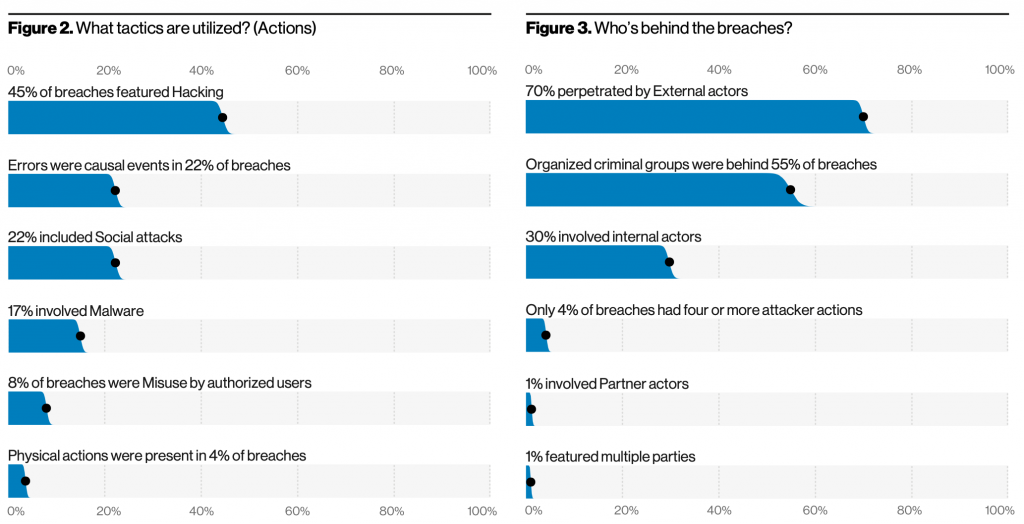
Verizon Data Breach Investigations Report
With data from real breaches and incidents, gain insights into the criticality of a robust cybersecurity program. Some sample statistics are included below, however the full report can be found here: Verizon DBIR.