Protect your brand. Reduce phishing attacks. Improve email delivery.
Is this legitimate or is someone trying to deceive your staff? Email Authentication Management aims to prevent spoofing attacks such as the above example.
Attackers commonly seek out businesses that do not have receive-side verification protections in place. Without proper configuration, anyone on the Internet can manipulate email and email servers to impersonate a legitimate domain name. Bound Planet’s EAM service assists in implementing and monitoring this configuration so that spoofing attacks are rejected by the receiving server.
Bad actors largely rely on phishing or spoofing attacks which can evade standard anti-spam solutions. In the example pictured above, there is no malware or links. These messages often aren’t caught by spam filters, and they look like legitimate e-mail. They simply take advantage of our productive human nature. This can lead to damaged reputations, data theft, downtime, and more.
EAM Illustrated
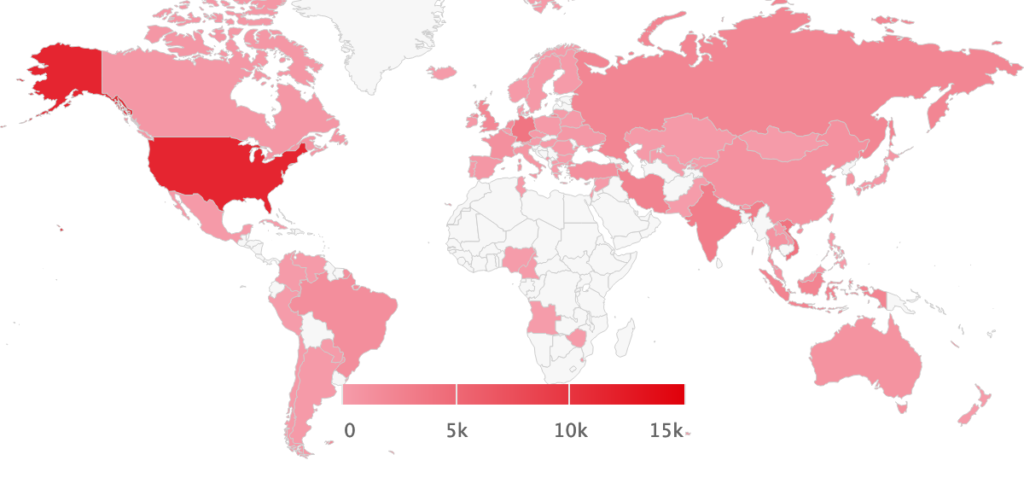
This image shows a report from a domain that is protected by Bound Planet’s EAM service. Spammers send email that spoofs this domain to the tune of nearly 6000 messages per day. The countries are highlighted based on source IP address of the sending system. Prior to implementing Bound Planet’s EAM service, these messages may have been delivered to unsuspecting victims. By fully implementing Bound Planet’s EAM, these spoofed messages are now typically rejected by the receiving server.
Attack Methods
Sending an email invokes use of various mail delivery protocols which mail servers use to communicate. In that communication process, the sending server identifies itself, the sender, the recipient(s), and other details such as the subject and message body. Cyber attackers can manipulate that exchange to make mail appear to originate from any source they choose. The email client renders the “From:” field per the cyber attacker’s specification, so a piece of email could appear to be sent from anyone: a CEO, CFO, HR, and others.
Solution
It is up to the domain owner to tell the Internet how to handle email it receives from their domain. There are three related email authentication mechanisms that must be configured for each mail source for a particular domain. These are SPF, DKIM, and DMARC. Typically, only SPF may be configured, but not in all cases. Organizations using Google Workspace/Gmail or Microsoft 365 may have DKIM signing enabled and an SPF record, however DMARC will not be configured by default.
SPF (sender policy framework) states that servers receiving a piece of email should check a record published by the sending domain owner which declares servers authorized to send for that domain. The receiving server can then check to see which policy is published and deliver or reject mail accordingly.
DKIM (DomainKeys Identified Mail) states that the sending mail server will sign mail with a signature that the domain owner publishes. When an email is received by a mail server, the signature on the message is checked against what is published by the domain owner. If the signature does not match, the receiving server can reject the message.
DMARC (Domain-based Message Authentication, Reporting and Conformance) takes care of checking differences between SPF, DKIM, and the “From:” field in a message. Messages that fail alignment are rejected with a proper policy in place. DMARC supports reporting so that receiving servers can identify when an email either passes or fails alignment.
Assess –> Implement –> Manage
This is where Bound Planet comes in. We assist organizations in fully achieving DMARC compliance to protect against spoofing, brand/reputation damage, and to improve email delivery. We work to identify sending sources and mail volume, configure DNS records and DKIM signing for each source, implement a reject policy, and finally monitor the implementation going forward. Our Email Authentication Management service simplifies the implementation process from start to finish.
References to EAM
Implementing receive-side verification techniques can be found in best practice guidance, and some organizations are required to implement this protection. Here are some additional places it can be found:
- CIS 9.5 IG2 and IG3 – Implement DMARC
- CISA CPG 2.M – Email Security
- DHS BOD 18-01, “Enhance Email and Web Security”
- Cyber insurance requirements
