Have you ever had 266 strangers try to open your front door 6,607 times over the course of a day? 😱
I found this to be somewhat interesting. I exposed a common service (ssh) on an Ubuntu VM to the Internet and observed 6,607 invalid login attempts in one day. The below chart shows top user names by number of attempts. You can see some usernames that might be worth reviewing. Often, attackers can make better guesses by enumerating what type of system is in use.
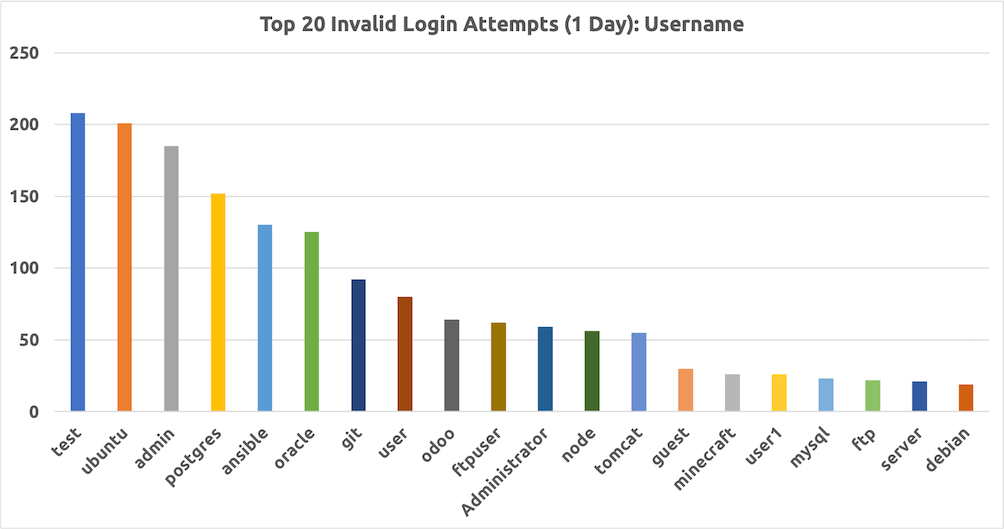
There were 1,742 unique usernames in total and 266 unique source IP addresses. The top IP address made 768 attempts. The remainder of the top 20 averaged 38 attempts. The top 20 included nine unique countries based on geo-IP lookup.
There was likely zero human interaction required on the part of those making the attempts. If one service on my tiny little server sees this volume, what is the impact on your systems?
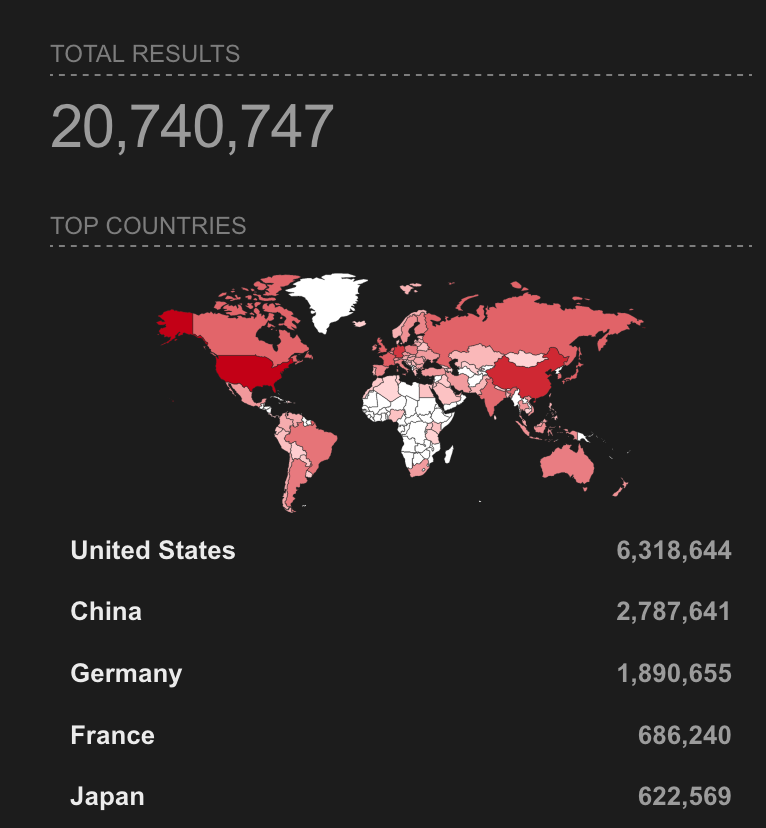
Food for thought: A simple Shodan search shows over 20 million systems on the Internet running ssh:
Here are some questions I might ask if I see a system exposed to the Internet:
-Should the service be exposed in the first place?
-Can the service be limited to specific sources/destinations?
-What protections/architecture influences the path to the exposed system?
-Do you have logging in place? What is your logging retention? Are logs reviewed?
-Can you detect and investigate this type of activity?
-Do you have strong authentication mechanisms in place?
-Do you have access controls such as account lockout after a defined number of attempts?
-Have you moved away from configuration defaults? Is configuration hardening in place?
-Are there vulnerabilities present that require no authentication considerations?
-Do you have a patching strategy and flaw remediation procedure that can address new advisories?
