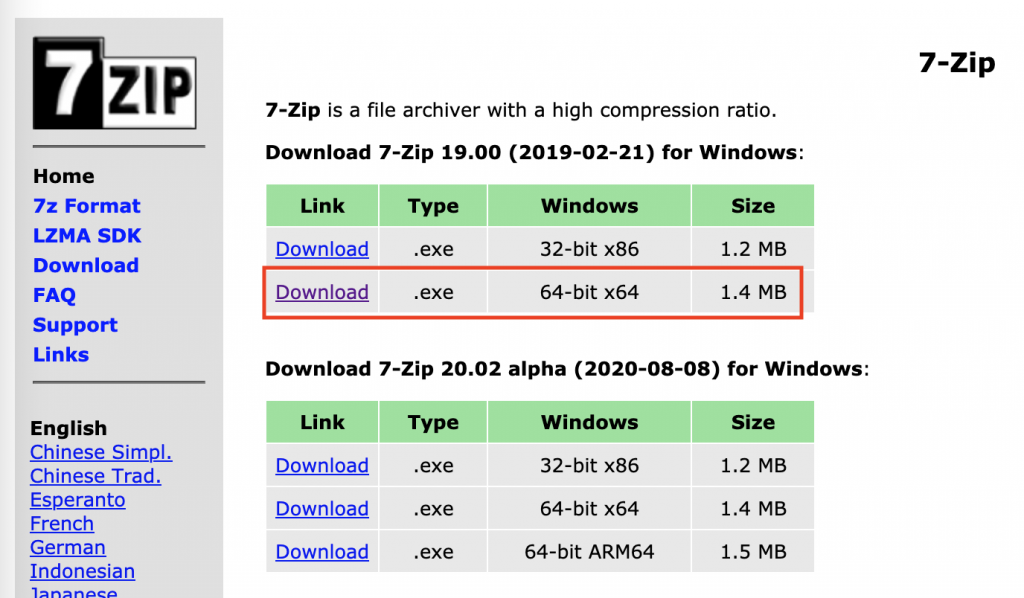
IT professionals and power users employ all sorts of utilities for daily tasks. Often, a quick search will suggest several options that might work for what is trying to be accomplished. Download the file, install the program or run the .exe, and all is well, right?
You might have downloaded this utility hundreds of times. You might be banking on your local anti-malware solution to be your guardian angel. What if someone embedded a payload in the most recently compiled version of this utility? Or somehow you downloaded it from a web page that is masquerading as the developer’s page and it contains malicious code?
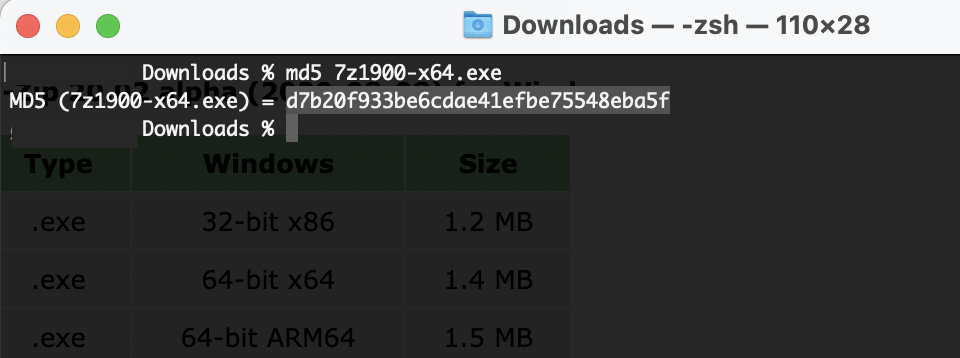
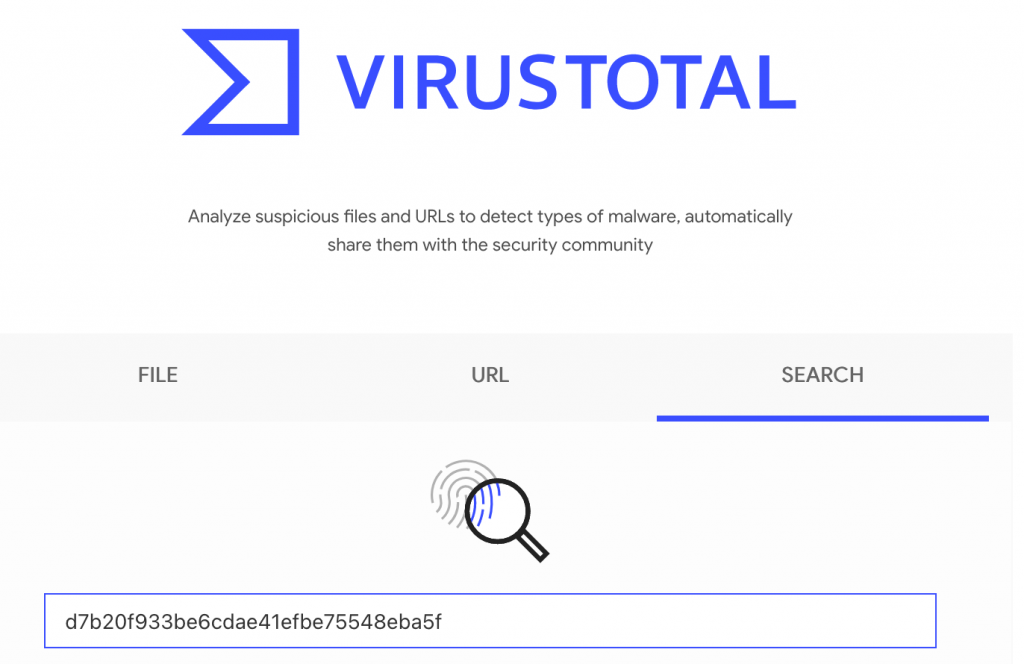
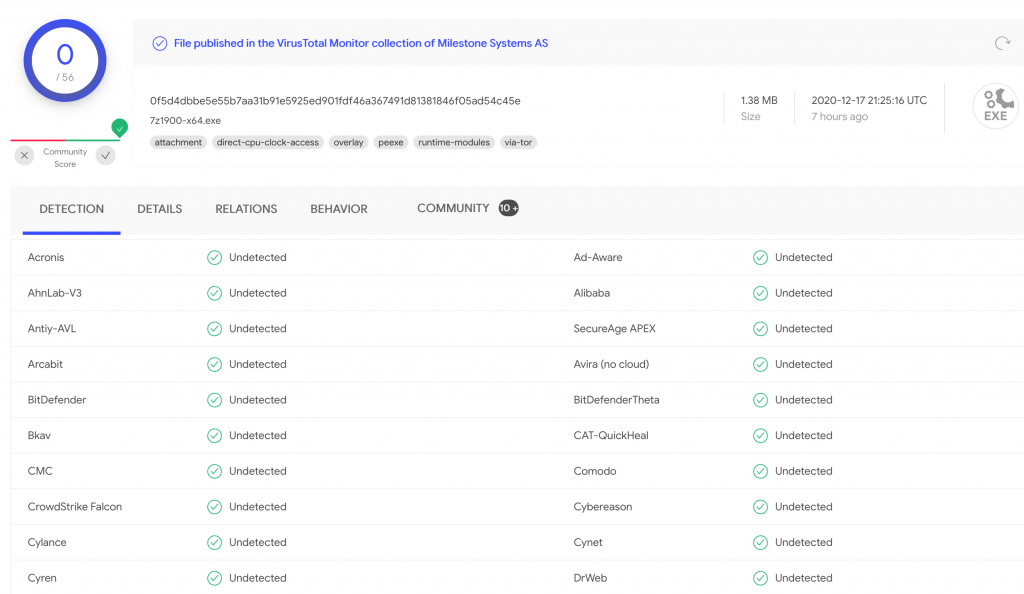
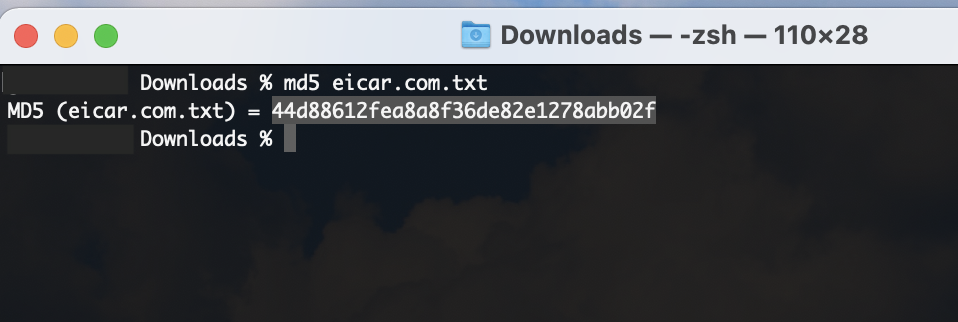
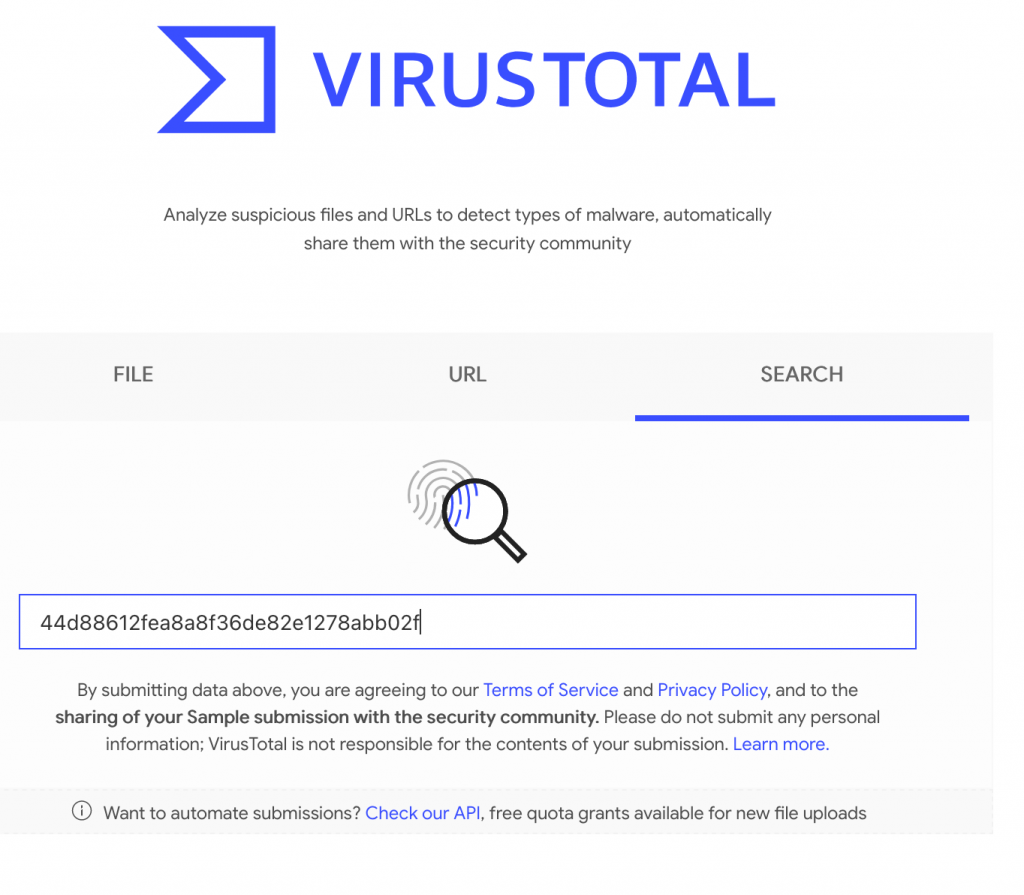
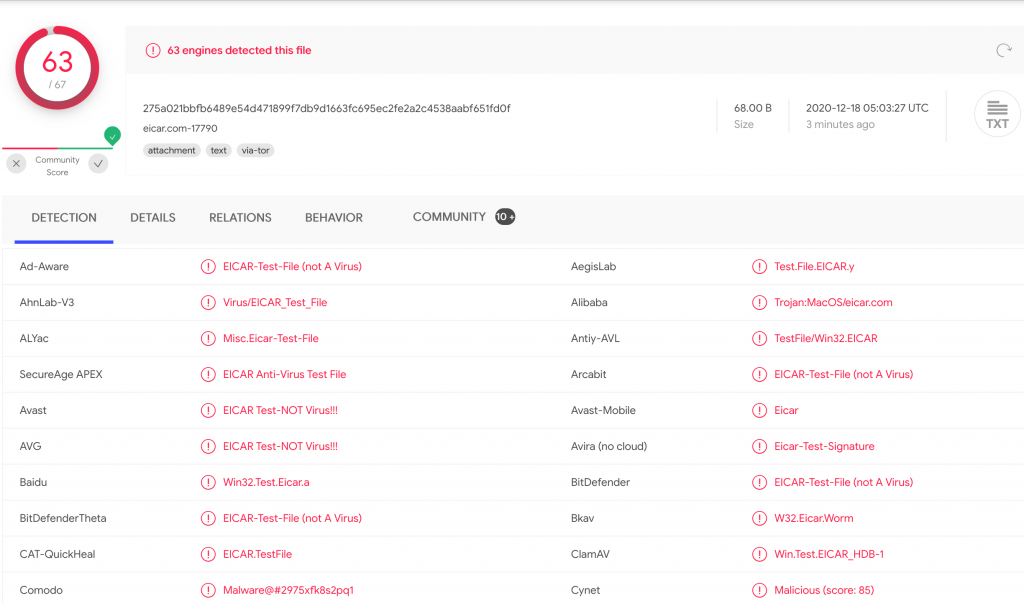
You can quickly receive 70+ opinions on the file you have downloaded by browsing to VirusTotal. Compute the hash of your local file, paste into the search engine, and you will have instant feedback as to the validity of your download.
This particular exercise ties well into the CMMC Maturity Level 3 Maintenance Practice MA.3.116: Check media containing diagnostic and test programs for malicious code before the media are used in organizational systems.
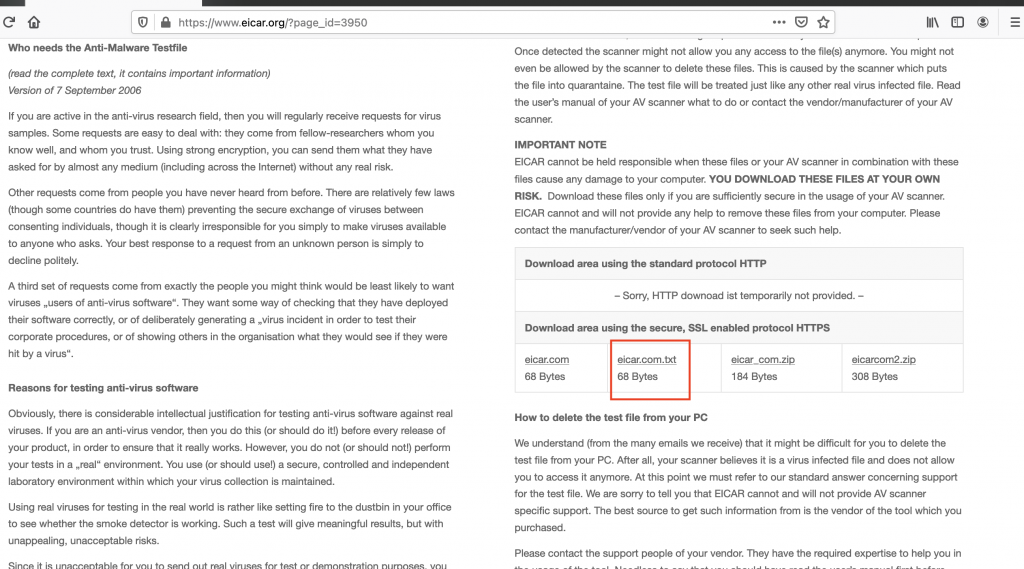
Examples: Good old 7-Zip and an Eicar test file.