Uncover hidden threats. Understand your attack surface. Prioritize remediation efforts.
Identify and prioritize security weaknesses across your technology infrastructure, drastically reducing your attack surface. Regular vulnerability scanning ensures you stay ahead of emerging threats, securing your systems and critical data.
Key Benefit:
Cost-Effective Risk Reduction: Offers a continuous and scalable method to identify a high volume of common security flaws, enabling efficient patching and remediation efforts that significantly reduce the attack surface.
What We Provide:
- Point-in-time or periodic scanning and assessment
- Remediation prioritization and guidance
- Internal and external scans
- Relevant reports and engagement deliverables
Risks Addressed:
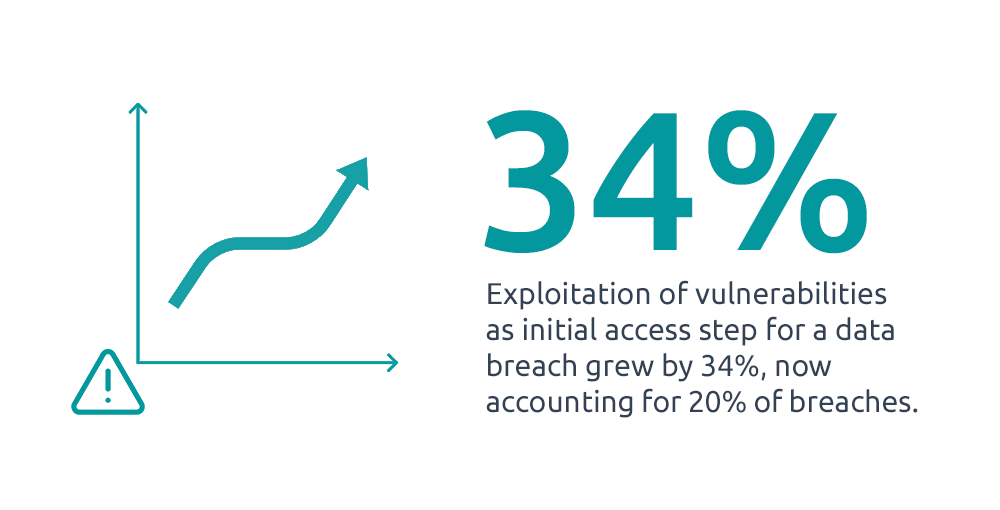
- Known Vulnerability Exploitation
Applicable Cybersecurity Framework Requirements (non-exhaustive list):
- CIS 7.5: Perform Automated Vulnernability Scans of Internal Enterprise Assets
- CIS 7.6: Perform Automated Vulnerability Scans of Externally-Exposed Enterprise Assets
- CMMC RA.L2-3.11.2: Vulnerability Scan
- ISO 27001:2022 A.8.8: Management of technical vulnerabilities