Attention M365 customers! Default Microsoft 365 Exchange Online settings are highly likely to permit spoofing in spite of any safeguards in place.
Be sure to investigate your settings and disable this feature if it is not needed, preventing attacks against your system.
The issue is related to the Direct Send component of M365 Exchange Online. It is being used to bypass all filtering and configuration to deliver phishing email. In our initial discovery activity, we discovered a Varonis blog post confirming what we were seeing:
https://www.varonis.com/blog/direct-send-exploit
In our own investigation, prior to being aware of a broader campaign, the initial report of spoofing was puzzling because the majority of anti-spoofing safeguards were in place, yet email was still being delivered directly to specific recipients in the organization. Upon review of the message headers, we began searching for similar behavior and found the Varonis article.
Please don’t hesitate to reach out if you need assistance!
How to check your settings
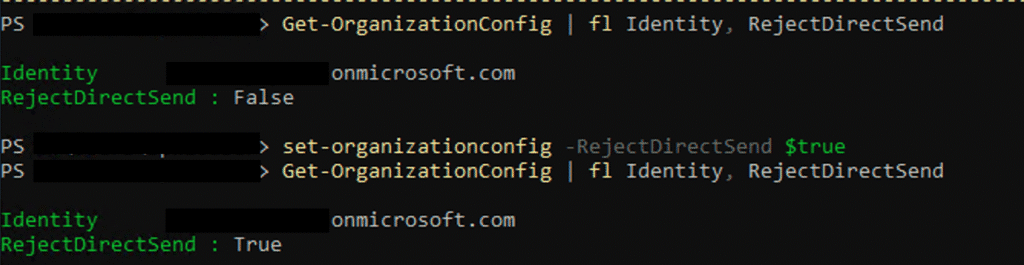
If you are comfortable with PowerShell and have the ExchangeOnlineManagement module installed and connected to Exchange online, you can observe your current setting using this command:
Get-OrganizationConfig | fl Identity, RejectDirectSendA value of False means that you are vulnerable.
To enable the RejectDirectSend setting, run this command:
Set-OrganizationConfig -RejectDirectSend $trueRun the above Get-OrganizationConfig again to validate the setting.
**NOTE**
You may need to migrate systems that use M365 to a different delivery mechanism, highlighted here:
Further information on Direct Send: